Caesar Cipher Report
Introductions
Caesar Cipher is one of the earliest known examples of
the Substitution Cipher Technique. It is said that Julius Caesar uses to
communicate with his army secretly by making use of this. Each Character of
plaintext messages is replaced by a character n position down in the alphabet.
The main motive behind this project is to introduce the Caesar Cipher technique which is the Substitution Cipher technique that is generally been used to encrypt the plaintext into a Ciphertext and then send and then decrypt it again to gain access to plaintext again. The advantages of using Caesar Cipher is that it’s easy to memorize and implement as well as simple to write and protect. The disadvantages are sometimes it’s easy to predict by other users.
Prerequisites
Here are the terminologies use:
Cipher
– Algorithm for transforming plaintext to ciphertext
Plain
text - The original message
Cipher
Text – The coded message
Key
– Information used in Cipher known only to sender/receiver
Encipher
(Encrypt) – converting plaintext to Ciphertext
Decipher
(Decrypt) – Recovering plaintext from Ciphertext
EXAMPLE:
Ø The first row denotes the plaintext
Ø The second row denotes the ciphertext
Ø The ciphertext is obtained by “shifting” the original
letter by n position to the right.
Ø In this example, it is shifted by 3 to the right
Ø A becomes d
Ø B becomes e
Ø X becomes a, and so on…
|
A |
B |
C |
D |
E |
F |
… |
X |
Y |
Z |
|
d |
e |
f |
g |
h |
i |
… |
a |
b |
c |
CONCEPTS OF PROJECT
Class:
A class is a category of objects that have similar
properties. It is a template or model from which you create objects. It is an an object that is rational. This may not be physical.
Scanner:
The scanner class is often used to scan the input and
interpret primitive (built-in) information types such as int, decimal, double,
etc. The scanner class returns the tokenized input depending on some pattern of
delimiters.
If-Else:
An assertion alone tells us that if a condition is
valid, a block of statements will be executed and if the condition is
incorrect, it won't. But what if the condition is wrong, we try to do something
else? The other declaration arrives here. We will use the other states to
execute a block of code while the condition is wrong for the other states.
String:
A string is simply an entity in Java that describes
the sequence of char values. A character list functions the same way as a Java
string. A vector includes a series of characters that are surrounded by
double-quotes.
For Loop:
A control flow assertion that iterates a component of
the programs several times is the Java for a loop. If the iteration number is
set, it is advised to use it for the loop.
PROJECT DEPLOYMENT
Syntax (od concepts used)
Class’s Syntax:
SYNTAX:
Class SampleCode {
public static
void main(string[] args) {
system,.out.println(“Hello”);
}
}
Scanner’s Syntax:
SYNTAX:
public class Main
{
public static void main(String
args[]){
Scanner in = new Scanner
(System.in);
System.out.print
("Enter a String: ");
String
mystr = in.nextLine();
System.out.println(“I’m
doing my B.Tech from " +
mystr);
in.close();
}
}
If-Else’s Syntax:
SYNTAX:
class Demo {
public static void main(String
args[])
{ int i = 20;
if (i
< 15)
System.out.println("i
is smaller than 15");
else
System.out.println("i
is greater than 15");
}
}
String:
SYNTAX:
public class MyClass {
public static
void main(String[] args) {
String txt = "Hello World";
System.out.println(txt.toUpperCase());
System.out.println(txt.toLowerCase());
}
}
For Loop:
SYNTAX:
class Main {
public static void main(String[] args) {
int n = 2;
// for loop
for (int i = 1;
i <= n; ++i) {
System.out.println("Java is fun");
}
}
}
Glimpse of Code
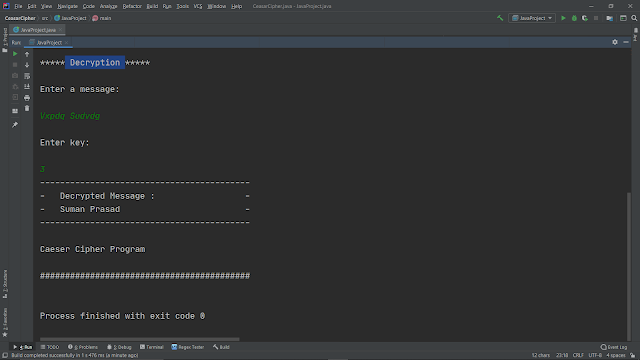
Proposed Output:
Expected Output:
Plots and Charts (Flow Diagram):
References:
[Accessed 9th December
2020]
2.https://www.theserverside.com/definition/Java-IDE
[Accessed 9th December 2020]
3. https://en.wikipedia.org/wiki/Caesar_cipher
[Accessed 10th December
2020]
4.https://commons.wikimedia.org/wiki/File:Caesar3.svg
[Accessed 11th December 2020]
5. https://commons.wikimedia.org/wiki/File:Caesar_cipher_left_shift_of_3.svg
[Accessed 13th December
2020]
6.https://randerson112358.medium.com/programming-encryption-algorithms-520cb98c039d
[Accessed 13th December 2020]